Encryption for Mobile Devices: Balancing Convenience with Data Privacy

Encryption for Mobile Devices: Balancing Convenience with Data Privacy
Mobile devices have become a necessity in our daily lives. However, with the proliferation of data collection and sharing on these devices comes growing concerns about privacy and security. Proper encryption techniques are mandatory to safeguard sensitive user information.
In this article, we will examine what encryption is for mobile devices and its benefits, the best practices developers use to keep mobile security tight but not a headache for the users, and how leaders in the industry are working to balance security with usability.
What is Encryption?
Encryption is a process of encoding data with an algorithm and encryption key to make it unreadable without decrypting it first. Full disk encryption (FDE) encrypts all the data on storage devices like hard drives, smartphones, or tablets automatically. Without decrypting it with the right key, the encrypted data is inaccessible.
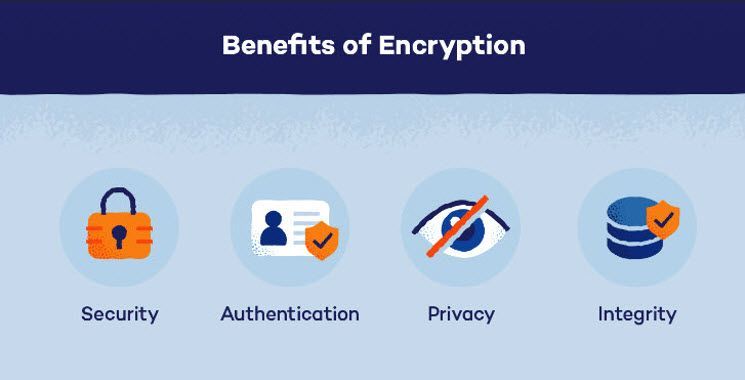
Benefits of Mobile Data Encryption
Some key benefits of encryption for mobile devices include:
Prevent Data Theft
One of the biggest benefits of encryption is preventing data theft if a mobile device is lost or stolen. Without encryption, anyone can access all the data on a lost or stolen device simply by connecting it to a computer or other device.
Aside from that with encryption, all the sensitive data like contacts, messages, photos, passwords, banking details etc. are rendered useless without the decryption key.
Even if hackers or thieves gain physical access to an encrypted device, they cannot decrypt and access the data without the valid decryption key.
Ensure Regulatory Compliance
Many privacy regulations, like the General Data Protection Regulation (GDPR) in Europe and the Health Insurance Portability and Accountability Act (HIPAA) in the US, require organizations to implement appropriate security controls to protect personal data.
Mobile data encryption is a very effective way to comply with such regulation's requirements for securing sensitive personal data.
It helps avoid penalties and fines for data breaches involving the loss of regulated personal data. Encryption provides verifiable proof that an organisation took the necessary steps to secure protected data.
Increase Security and Privacy
Encryption provides an additional layer of security compared to relying only on device locks and passwords. Even if unauthorised access is gained to a device bypassing other controls, the data will remain encrypted and useless without the decryption key.
It protects against software and operating system vulnerabilities that could potentially allow hackers to access data.
Encryption also prevents unauthorised access to data through covert techniques like taking physical possession of a lost device, acquiring backups in transit, or breaching cloud services.
How do Android and iOS Handle Device Encryption?
Both Android and iOS use strong data encryption but differ slightly in implementation:
Android Encryption
Android uses device-specific encryption keys unique to each device. Both device keys and Google account keys are needed to access data. Android devices have been encrypted by default since Android 7.
Android 14 enhances file-based encryption with stronger algorithms to secure biometric data. It provides APIs for developers to implement encryption best practices. Regular security updates address vulnerabilities.
iOS Encryption
iOS uses device keys combined with iCloud account keys for tighter integration. Even with device access, the iCloud password is needed to decrypt user data.
The encryption key is protected by passcodes/PINs. Malware risks are lower due to app sandboxing and code signing during app deployment. Automatic security updates delivered by Apple enhance iOS security consistently.
Both platforms employ robust encryption to lock device data. However, proper key/password management and regular updates are necessary to keep evolving threats at bay.
What Best Practices Developers Implement for Mobile App Security and Encryption?
Here are the key mobile app security best practices that developers follow:
Secure Development
Developers use standardised IDEs like Android Studio and Xcode to minimise vulnerabilities compared to unofficial tools. It helps leverage encryption and access control APIs securely.
Encryption
Sensitive data is encrypted both at rest and in transit using strong algorithms like AES-256 and RSA via platform encryption APIs and libraries. Random initialisation vectors and salts increase crypto strength.
Access Controls
Authentication methods like biometrics, tokens, and 2FA protect access, combined with role-based least privilege models that restrict features. Re-authentication enforces extra security for sensitive operations.
Security Testing
Comprehensive testing through manual and automated means proactively identifies and addresses issues before public release. Regular post-release testing ensures ongoing security.
Key Management
Encryption keys are safely generated, stored, and transmitted out of the band without being hard-coded or logged. Standards like key rotation are followed.
Privacy and Response
A detailed privacy policy provides transparency into data handling practices to ensure ongoing compliance. Any vulnerabilities are prioritised and patched quickly according to disclosure policies.
Balance of Convenience and Security on Mobile Devices
While encryption and access controls enhance mobile security and privacy, certain trade-offs impact usability:
| Security Measure | Impact on Convenience |
|---|---|
| Increased Cognitive Load | Strong and frequent authentication using complex passwords takes more effort and time from users hampering convenience. |
| Limited Third-Party Sharing | Preventing unnecessary data access and sharing with third-parties reduces functional integrations impacting user experience. |
| Performance Overhead | Encryption/decryption and robust access validation consume computing resources slightly impacting device/app performance. |
To balance security and convenience, industries are looking forward to new approaches like:
- Biometric authentication for frictionless yet strong access.
- Single sign-on/federated identity for fewer logins across apps/services.
- On-device or edge processing offloading encryption overhead from devices.
- Granular share preferences controlling minimum data exposure.
- Usable security techniques educate users about threats and security best practices.
Conclusion
Encryption plays an important role in securing mobile devices and addressing evolving threats and regulations. While Android and iOS implement strong native encryption, developers too must incorporate best practices to responsibly handle sensitive user data. New techniques aim to balance encryption-provided security with usability. Collective efforts can help drive the right balance between mobile device data privacy and convenience over the long term.
Sources:
- https://www.inspiringapps.com/blog/92/mobile-device-security-data-protection-on-i-os-and-android/
- https://www.iolo.com/resources/articles/what-is-phone-encryption-and-the-benefits/
- https://www.securitymetrics.com/blog/securing-mobile-devices-mobile-encryption









