How to Recognise and Prevent Phishing Attacks: A Beginner's Guide

Almost 83% of UK businesses that suffered a cyber attack in 2022 reported it to be phishing. This highlights that phishing attacks are a major threat, not just for businesses but for everyone in the online world.
Phishing scams aim to steal your personal information and financial details or even hijack your accounts. But fear not! This blog post explores how to recognise them along with some key prevention strategies so you can significantly reduce your risk of falling victim.
Let’s get started.
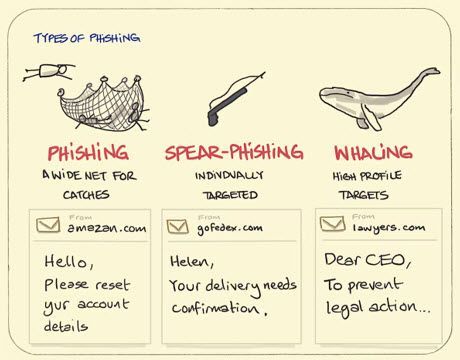
Common Types of Phishing Attacks
Here are some types of phishing attacks that are quite common:
- Email phishing: It’s the most widespread form of phishing, where hackers impersonate a legitimate firm to trick you into providing sensitive information. Approximately 35% of ransomware attacks originate from emails.
- Spear phishing: Spear phishing is different from broad malware attacks as it targets any specific individual or organisation. To make it look genuine, attackers use the personal information of the targeted entity. It is responsible for almost 66% of all data breaches.
- Whaling: Targeting high-profile individuals like executives, whaling involves attackers who impersonate someone the victim may trust. Its basic goal is to obtain crucial data from corporate networks.
- Smishing: Smishing refers to fraudulent SMS messages that may trap the recipient into providing personal information. Sometimes, it’s also used to install malware on a device to keep tabs on business or personal communications.
- Vishing: Also known as voice phishing, vishing allows hackers to extract the victim’s financial details via phone calls. Usually, they act like official authorities, such as bank officials or government bodies, to win trust.
How to Detect Phishing Attacks - 7 Signs to Look Out For
Some signs that indicate a phishing attack are described as follows:
- Suspicious email addresses and domain names: Phishing emails come from accounts or domain names that might look like that of a legitimate company at one glance. However, with deeper investigation, you can spot slight alterations in spelling or domain extensions.
- Urgency and fear-inducing messages: Emails intended to steal your personal data commonly use urgent language. They may claim that there’s a serious issue that needs your immediate attention, or else you’d have to face severe consequences.
- Bad grammar and spelling errors: Legit organisations will never send over emails with grammatical issues. While a single typo may occur mistakenly, professional emails with numerous errors are a big red flag.
- Claims to be a government agency: A government agency would not contact you directly through any digital communication channel. It usually sends official letters to home addresses. Thus, never click any message or email with such a claim.
- Doubtful attachments: Be cautious of every email attachment, especially if the sender is unknown. The risk increases when such files have an unfamiliar extension like .zip, .scr, or .exe. Downloading them can provide an entry point for malware to enter your device.
- Unrealistic offers: If you see an offer that seems too good to be true, trust your instinct. Phishers attract victims by promising to offer rewards. For example, you may receive a message saying you have won a lottery that you didn’t even enter.
How to Prevent Phishing Attacks - 7 Tried-and-Tested Ways
Let’s explore some proven tips to stay safe from phishing attacks:
1. Do Not Click Suspicious Links
No matter how genuine an email looks like, never click on any link contained in it that appears suspicious. Doing so can lead you to fraudulent websites that can hack your personal details.
To inquire whether a link is legit or not, you can use the hover technique. Simply move your mouse over the link to see the actual URL. If it matches with that of a legitimate source, you can click on it safely.
2. Implement Multi-Factor Authentication (MFA)
Through MFA, you can enhance the security of your online accounts as it requires two or more verification factors to log in. The factors typically include a password, biometric scan of fingerprints, or any hardware token.
This implies that even if phishers obtain your credentials through an attack, they won’t be able to cross MFA and steal your personal data.
3. Give Security Awareness Training to Employees
Businesses shall offer security awareness training to their workers to combat data breaches caused by phishing attacks. They must teach them the ways to identify and avoid such incidents. Moreover, there should be an extra emphasis on discouraging employees from sharing any company-related details on social media.
Practical exercises like simulated phishing or social engineering attacks can be highly effective in this scenario. Through these, workers can practice applying the training’s objectives in a safe environment to evaluate how they might react in a real situation.
4. Download an Anti-Phishing Toolbar
An anti-phishing toolbar runs checks on every site you visit and compares that to the black-listen ones known to be involved in phishing. As soon as you are about to visit a harmful webpage, the toolbar will instantly alert you.
Here are some common examples:
● Netcraft Toolbar
● Avast Online Security
● McAfee WebAdvisor
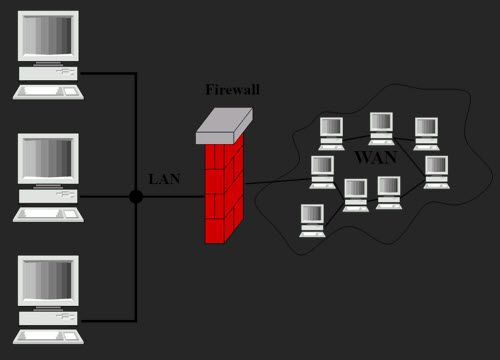
5. Use High-Quality Firewalls
A firewall refers to a security software that monitors incoming and outgoing traffic to allow or stop it based on a defined set of security rules. It can prevent you from becoming a phishing victim by blocking access to malicious URLs.
Furthermore, modern firewalls like Next-Generation Firewalls come with additional security features, including Deep Packet Inspection and Intrusion Prevention System. These technologies can analyse the data passing through the network for malicious content associated with phishing, like fake authentication requests.
6. Apply Spam Filters to Emails
Spam filters are such tools that can detect unwanted and potentially harmful email messages. Basically, a set of algorithms identifies whether an email is safe enough to be delivered to your inbox or it should rest in the spam folder.
These filters have a list of spam and phishing domains, and they block emails from such sources. They also scan URLs and attachments for malicious content.
7. Update Systems Regularly
Last but not least, make sure your device system is updated, as software vulnerabilities also increase the chances of success for phishing attacks. With updates, the system’s security features get enhanced, which makes it more robust. This might include improved filtering techniques, better anomaly detection, and stronger encryption.
Moreover, if a phishing attack is successful, outdated systems can make it easier for malware introduced into the system to do the damage. Contrarily, updated systems are more likely to resist such secondary attacks or limit their damage.
Wrapping Up
In conclusion, phishing scams can be tricky, but by staying vigilant and following a few simple steps, you can recognise and avoid them. With a little caution and some helpful knowledge, you can keep your information secure and out of the hands of scammers.
If you ever suspect a phishing attempt, you must report it to the appropriate authorities, such as your Internet Service Provider or the national cybersecurity centre. Also, don’t forget to spread awareness among your family and friends to help them stay vigilant against similar threats.









